We’re excited to announce the release of version 1.36 of FusionAuth. It shipped in mid April, 2022. The 1.36 releases include bug fixes, a new Identity Provider, and SCIM support.
These releases contained features, enhancements, and bug fixes. Please see the release notes for a full breakdown of the changes between 1.35 and 1.36.
There are a few improvements that I wanted to call out specifically.
SCIM 2 support
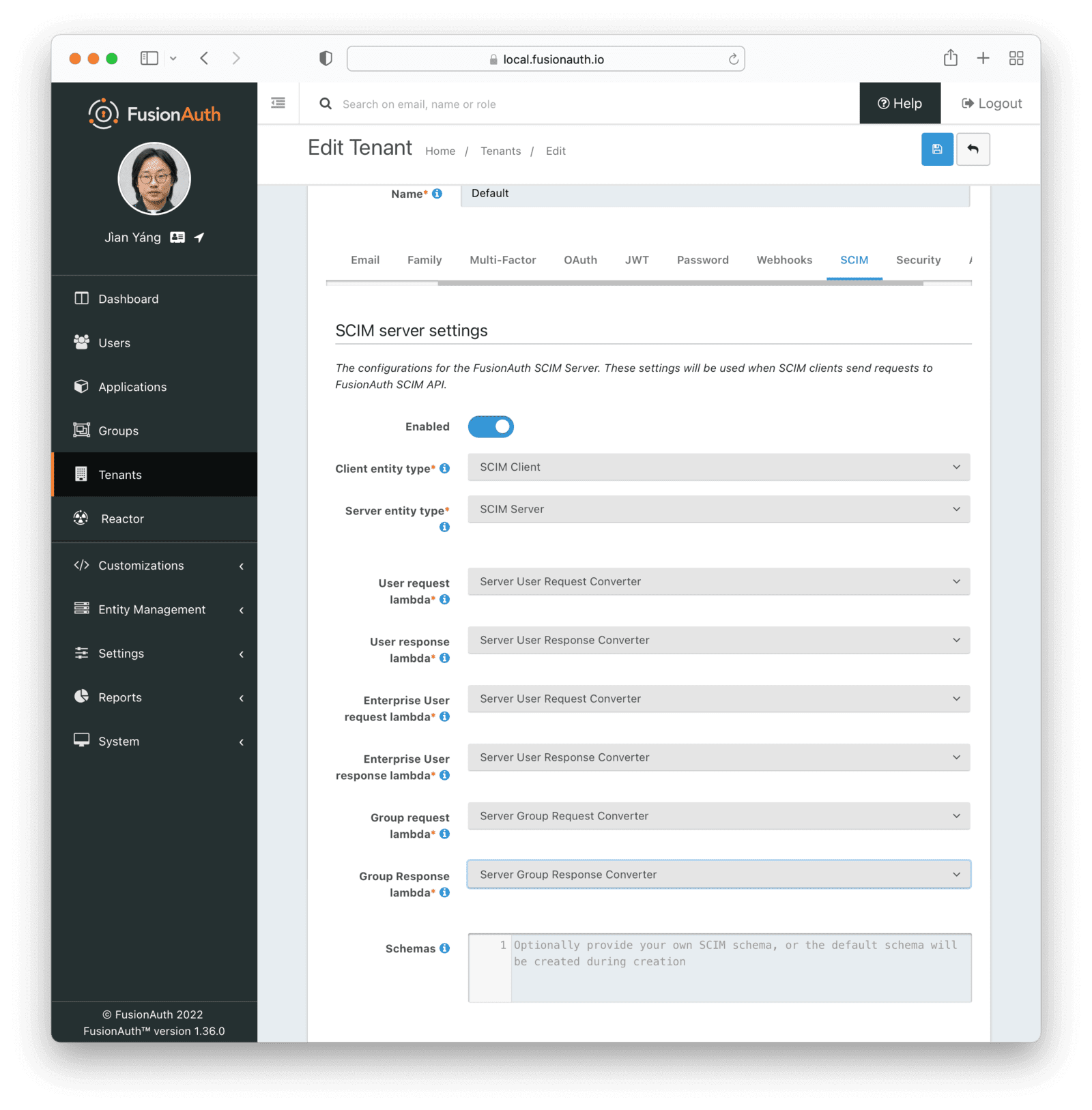
SCIM 2 (System for Cross-domain Identity Management), a standardized API for identity management sponsored by the IETF, allows user records to be read, written, and shared via HTTP using a simple JSON schema. In a long-awaited feature, FusionAuth now supports SCIM formats and operations as well as our own API.
This feature is particularly helpful in cases where you want to use a third-party SCIM-compliant backend to provision users and keep user data in sync. SCIM helps you manage users across systems like GitHub, Salesforce, and Trello, among others.
SCIM data formats vary wildly so new lambdas are available. The lambdas will take care of mapping from the SCIM provided user data into the FusionAuth user data schema and vice versa. This allows for a large degree of integration flexibility.
This functionality is only available for our Enterprise users; learn more by visiting the pricing page or contacting our sales team.
Nintendo Online Identity Provider
Nintendo Online has been added as an identity provider, allowing users to log in using their Nintendo Online accounts.
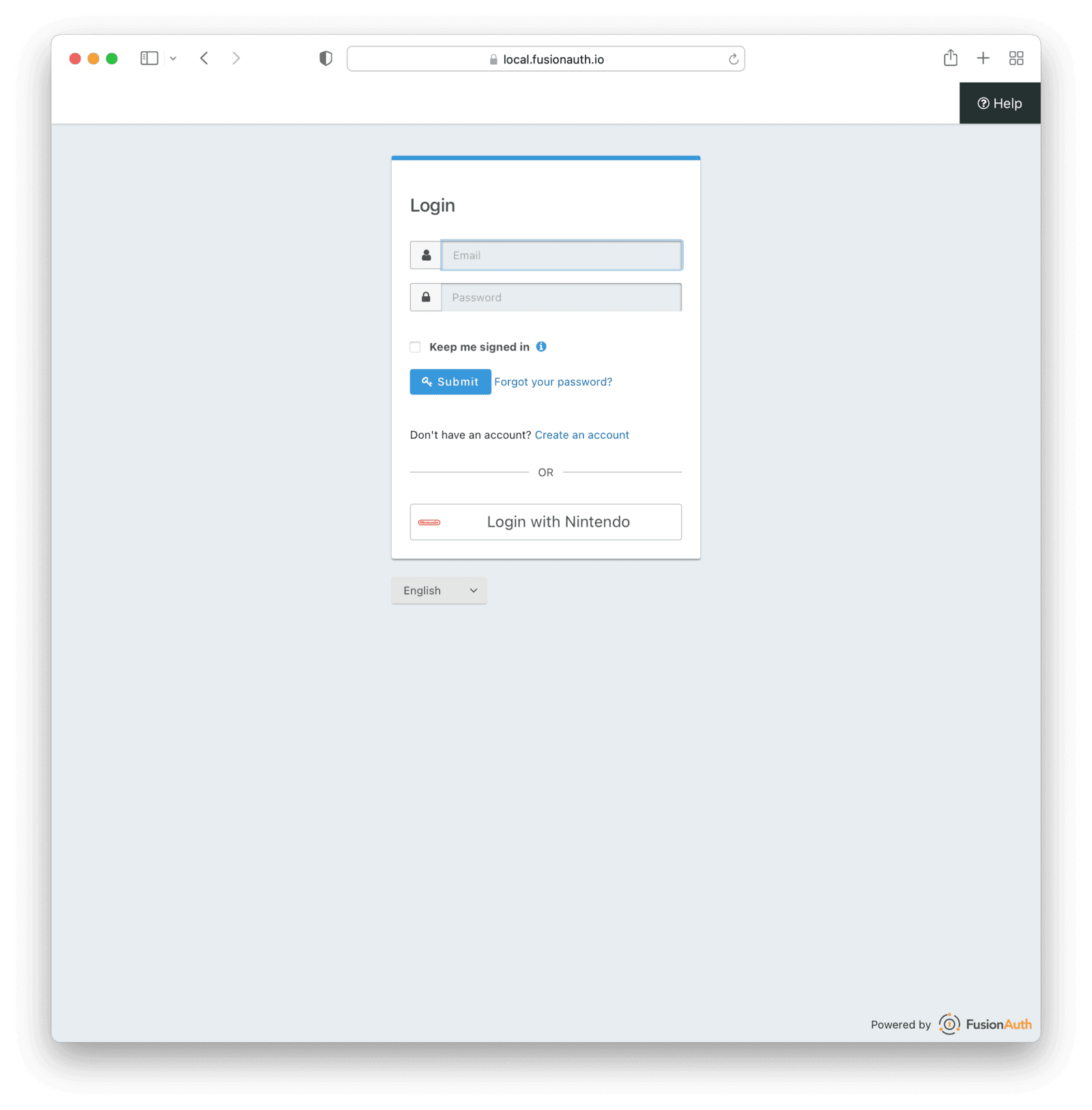
This feature is available to our Enterprise and Essentials license holders as part of the “Advanced and gaming Idp” suite. Learn more about these editions by visiting the pricing page or contacting our sales team.
Webhook for user identity provider linking events
A new webhook event is available for developers to trigger an action when a user links or unlinks an identity provider.
This will allow developers to write a subsystem that immediately notices any new IdP accounts their users associate with their FusionAuth account (e.g. Google, Facebook, LinkedIn) and when these accounts are unlinked from FusionAuth. Another system listens for those events and handles them: for instance it can record the data for analytics, or adjust functionality which is only available if you have an account at a certain IdP, like a special in-game item is only available to Xbox users.
A typical user scenario might go as follow:
- A user, Alice, signs in to ExampleGame using ‘login with XBox’ and FusionAuth. A link event is sent.
- Alice plays ExampleGame for months.
- Alice sells her XBox and buys a PS5.
- Alice signs into ExampleGame with ‘login with PSN’. A link event is sent.
- Alice notices that there is an XBox account associated with her FusionAuth account. She unlinks the account from within the ExampleGame UX. An unlink event is sent.
Documentation for this web hook is available here.
The rest of it
There were 17 issues, enhancements, and bug fixes included in this release. A selection of these include:
- Custom password plugins that rely on dependencies in jarfiles are now more easily loaded. Required jars can now be placed in the same directory as custom plugin, and will be loaded in a separate class loader.
- OAuth2 Password Grant correctly returns MFA method.
- Support for higher volumes of logins when using a connector by making more conservative use of system resources.
Read more about all the changes in the release notes.
Upgrade at will
The release notes are a guide to the changes, fixes, and new features. Please read them carefully to see if any features you use have been modified or enhanced.
If you’d like to upgrade your self-hosted FusionAuth instance, see our upgrade guide.
If you have a FusionAuth Cloud deployment, proceed to the “Deployments” tab on your account dashboard and upgrade your instances. If you have any questions about the upgrade, please open a support ticket.
Or, if we’ve piqued your interest and you’d like to use FusionAuth, check out your options.










