Security
10 Steps To Secure Your Authentication System
By Mihir Patel
Building an authentication system can be both time and cost-intensive for system engineers. Traditionally, organizations have maintained servers dedicated to authentication. Nowadays, third-party authentication providers like FusionAuth help minimize internal maintenance costs and improve security by keeping up with modern best practices for their users.
Whether your authentication is built in-house or relies on a third-party provider, several specific factors are essential. These include speed, availability, disaster recovery, SOC 2 compliance, and security protocols to protect systems and user credentials.
The complexity of your authentication systems depends on the industry you operate in. If you’re in medical or healthcare, extra precautions are commonplace. Comparatively, regulations for social media companies are much less demanding.
Regardless of industry, all organizations should take steps to protect their systems. In this article, I’ll break down some of the essential steps developers need to take to maintain a secure authentication system. Some of these can be automated, while others are processes that will require work across departments, but all will increase the security of your auth system.
1. DevSecOps (Shift Left)
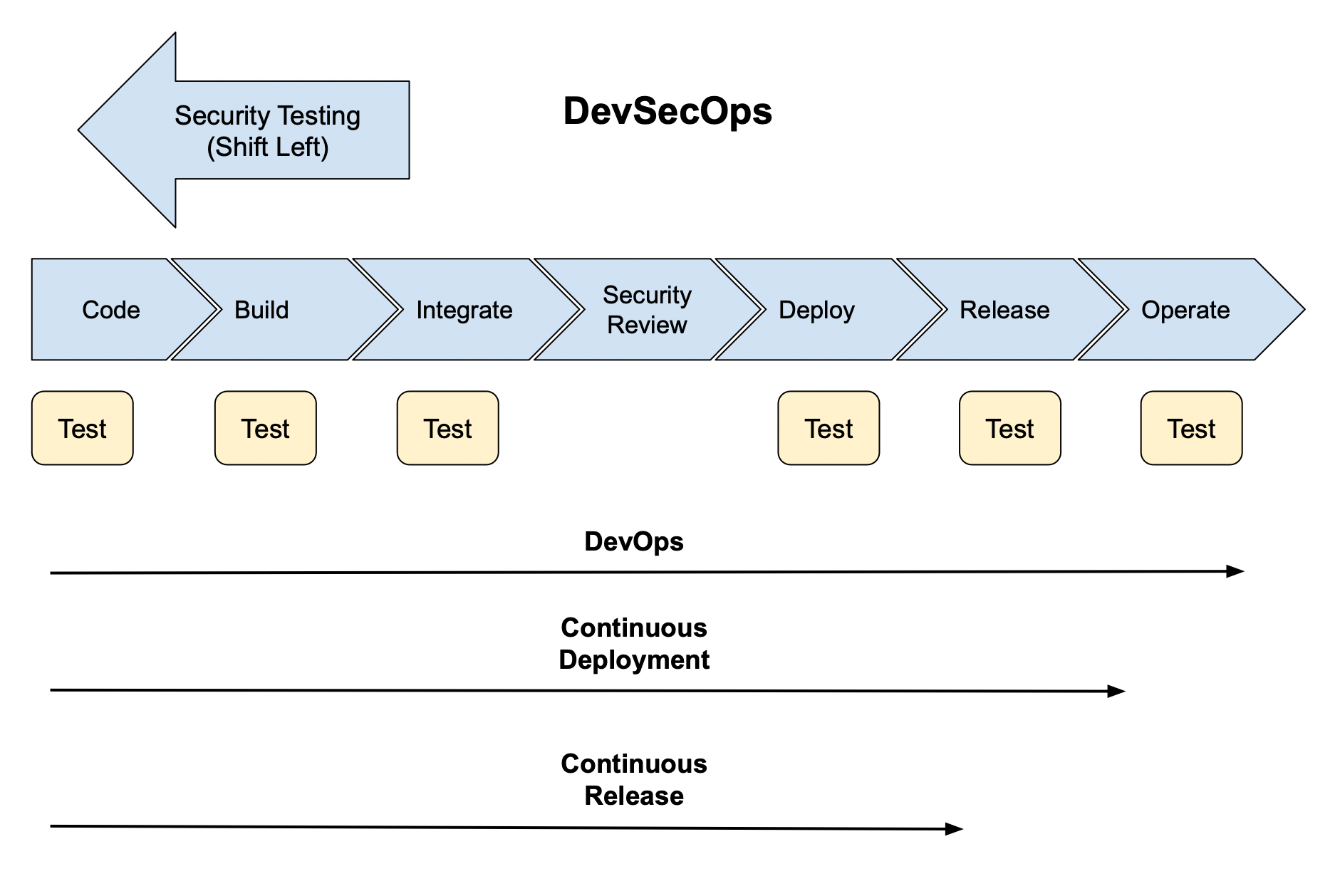
Ensure DevSecOps standards are set in place to allow for security testing during the early stages of development.
Traditional security testing happens just before or after the release. This can be too late for security testing. It can also lead to unexpected delays to critical deadlines if there are security issues to be found later.
DecSecOps dictates that rather than testing for security during or after release, security planning is introduced during each phase of the DevOps pipeline. This allows testing to happen earlier in the software development cycle. The benefit of this approach is the codebase is secure and tested for security before being accepted into the build.
DevSecOps does not replace traditional security testing.
Frequency: security checks should be run every time code is accepted to build that is ready to be released into production.
2. Regular Security Reviews
Information security reviews must be performed to identify and mitigate risks whenever a new infrastructure is stood up. Reviews must also be performed when significant changes are made to an existing system or when you’re permitting a third-party access to internal systems.
Security controls are implemented by the Information Security team, so developers should account for them while building or changing a system. For example, a developer should understand what cryptographic algorithms are approved for use within an organization. Going against a security policy can cause unexpected delays, so developers should perform information security reviews ahead of time.
Frequency: conduct whenever a new system is stood up or major changes are made to a system.
3. Static Code Analysis
Static code analysis is the analysis of code repositories performed without executing the code itself (analysis on running programs is called “dynamic analysis”). Static code analysis uncovers suboptimal and inefficient code, signaling engineering teams to fix the issues. This process means a team only ships quality, reliable code.
Static code analysis is not the same thing as a code review. Static code analysis is done by a machine, whereas code review is done by a human. Essentially, static code analysis is automated—code reviews are manual.
Some editors, such as Visual Code, contain built-in static analysis tools. A relatively complete list can be found on Wikipedia.
Frequency: run every time during PR merge or releases as a minimum. But if you don’t want to delay your releases, it’s best to run them during development.
4. Penetration Testing
A penetration test (pen test) is a brute force technique conducted by cybersecurity hackers to highlight vulnerabilities. Penetration tests are run by in-house employees or contractors who mimic the actions of an attacker.
There are three types of pen testing: white box provides the tester with all the details about an organization’s system, black box provides the tester with no knowledge of the system, and gray box provides the tester with partial knowledge.
Frequency: penetration testing should be done at least once a year.
5. Bug Bounty Program
A bug bounty program is a reward program offered by an organization that incentivizes the reporting of bugs and vulnerabilities. This is a great way to outsource discovery of security bugs from other developers. Large technology companies often run bug bounty programs—here’s Google’s reward program. Be clear about what you consider to be a valid bug and what kind of reporting is needed.
Frequency: the program should be available throughout the year, but you might want to check the budget with your finance team.
6. Prevent the Reuse of Passwords
It’s unfortunately convenient to use the same passwords over and over again as opposed to choosing something unique and more secure. And hackers are known to target users with similar passwords. According to Verizon Data Breach Investigations Report, compromised passwords are highly responsible for data breaches.
So it’s vital that organizations follow the standards of digital identity guidelines set by the National Institute of Standard and Technology.
Frequency: password guidelines should be in place to prevent users from using the same password.
7. Audit Access Logs
Audit logging detects a potential attacker’s activities, flagging anything suspicious. Log collection should be the responsibility of both security and software development teams. Logs are useful in assessing security incidents during post-mortem analysis.
Logs are also critical for monitoring. If you see unusual server traffic from an unrecognized IP address, you can quickly scan your logs to identify the unusual activity and mitigate risks and vulnerabilities sooner. To maintain system stability, ensure proper logs are being generated and audited by administrators, network engineers, and developers.
Frequency: auditing access logs should be frequent, using monitoring or some automation tool.
8. Implement Brute-force Protection
Hackers tend to use brute-force techniques to log in into your system. One of the most common techniques against this is IP-based user rate limiting. This requires preventing hackers from manipulating their IP address. If a user has made an attempt to log in several times, ask a user to complete a CAPTCHA test.
This does not ensure that it will eliminate brute-force logins. However, making the manual process as tedious as possible can encourage a hacker to give up.
Frequency: implement CAPTCHA test with every login attempt after a certain number of logins.
9. Implement Proper Multi-factor Authentication (MFA)
Multi-factor authentication requires at least two steps of identity verification, so it’s much more secure than password-based login. Passwords are vulnerable to hackers, so a password isn’t enough to verify online identity in today’s environment. Multi-factor authentication offers an extra layer of protection.
Be careful with SMS as a second factor. SMS-based 2FA can be abused in many ways if a hacker gets access to the password and the SIM card. For the best security, multi-factor authentication should be implemented using a dedicated app or a device that generates a temporary verification code.
Frequency: evaluate where MFA makes sense, based on your security needs. It may be needed every time someone logs in, every time they log in to a new device, or whenever they take a sensitive action such as changing their password.
10. Personnel Training on Phishing
Phishing is a technique to manipulate individuals to reveal their personal information using human psychology. A typical phishing example is the sending of fake emails that pretend to be from reputable people and organizations. According to the Verizon Breach Investigation Report, phishing is one of the most common ways of exposing critical systems and personal identities. Automation can help only so much, so people need to stay alert to phishing attacks.
To prevent phishing, you can provide interactive employee training to help employees detect and report phishing attempts. Depending on the size of the organization, IT can create simulated phishing campaigns to improve employee alertness around these malicious tactics.
Frequency: personnel training on security topics should be provided twice a year.
Conclusion
Authentication is critical in protecting your organization’s critical infrastructure. To sum up, security reviews, static code analysis, and penetration testing help expose vulnerabilities sooner during the development process. DevSecOps is a great practice to follow during the development operations cycle, too. Protecting infrastructure by properly implementing MFA is critical and limiting brute-force logins to critical systems and auditing logs frequently. You can outsource bug reporting by introducing a bug bounty program to external developers. Lastly, ensure you have a good process around security training.
Protecting your authentication system should be everyone’s concern within your organization, so ensure these steps are shared across the company if you want to keep your authentication system secure.