Thank you so much Dan, that was exactly the issue. I successfully verified a token with that secret. I appreciate it very much.
Best posts made by raghebmichael
-
RE: Manually verifying a JWTposted in Q&A
Latest posts made by raghebmichael
-
RE: Manually verifying a JWTposted in Q&A
Thank you so much Dan, that was exactly the issue. I successfully verified a token with that secret. I appreciate it very much.
-
RE: Manually verifying a JWTposted in Q&A
Something is very wrong. I don't know if this is something anybody else is facing, but I changed to a RS256 key and used the public key on jwt.io and it is still invalid. I cannot validate a JWT outside of /api/jwt/validate. This is a really big deal to me to be able to do something as simple as validating. Please let me know if I am in error, but if I can't get this to work I cannot continue using fusionauth and that's a big bummer to me as I had high hopes for this service.
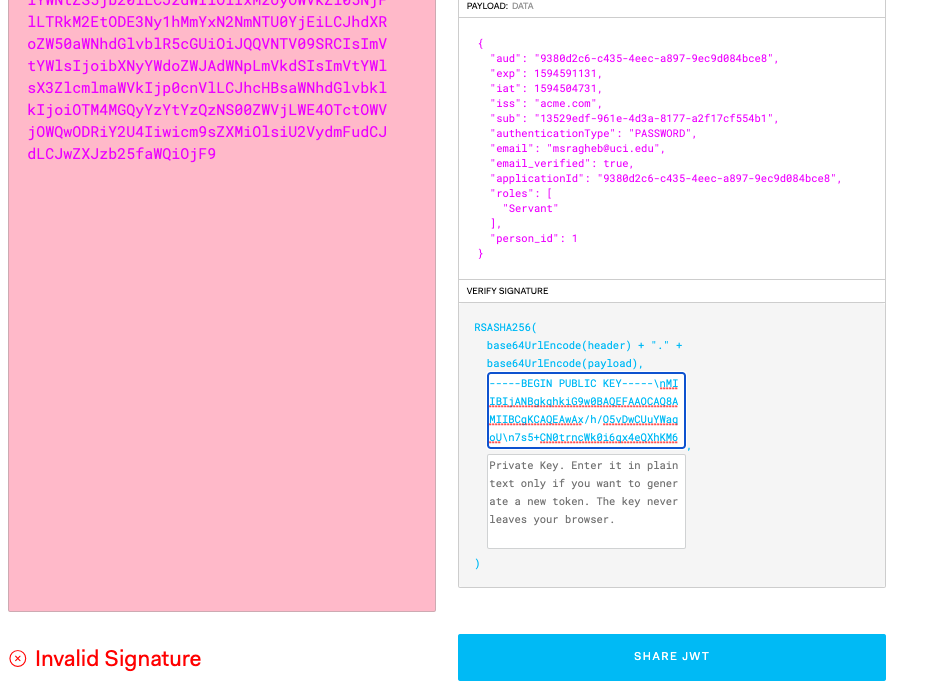
-
RE: Manually verifying a JWTposted in Q&A
I don't think it's an issue with server time. I can't verify the signature on jwt.io when using my secret and token.
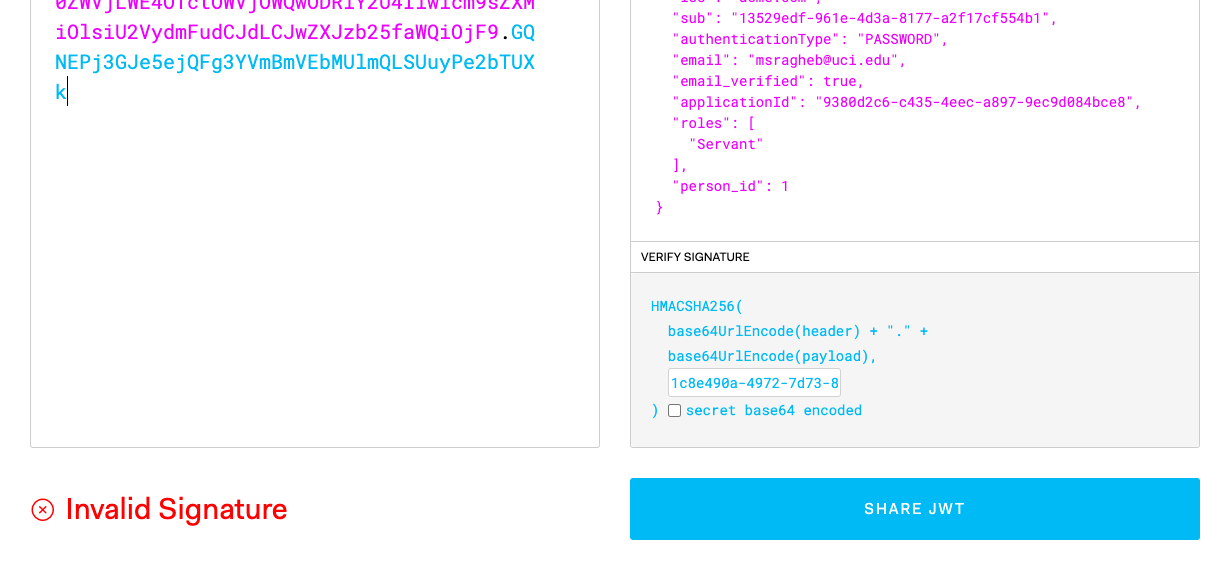
Here is the long lasting token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjllZDRjNjc1NCJ9.eyJhdWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJleHAiOjE1OTQ1ODU2ODYsImlhdCI6MTU5NDQ5OTI4NiwiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIxMzUyOWVkZi05NjFlLTRkM2EtODE3Ny1hMmYxN2NmNTU0YjEiLCJhdXRoZW50aWNhdGlvblR5cGUiOiJQQVNTV09SRCIsImVtYWlsIjoibXNyYWdoZWJAdWNpLmVkdSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJhcHBsaWNhdGlvbklkIjoiOTM4MGQyYzYtYzQzNS00ZWVjLWE4OTctOWVjOWQwODRiY2U4Iiwicm9sZXMiOlsiU2VydmFudCJdLCJwZXJzb25faWQiOjF9.GQNEPj3GJe5ejQFg3YVmBmVEbMUlmQLSUuyPe2bTUXk -
RE: Manually verifying a JWTposted in Q&A
@dan said in Manually verifying a JWT:
hmac_secret = '1c8e490a-4972-7d73-8935-06621a0a6441'
token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjllZDRjNjc1NCJ9.eyJhdWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJleHAiOjE1OTQ0ODk5NTMsImlhdCI6MTU5NDQ4NjM1MywiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIxMzUyOWVkZi05NjFlLTRkM2EtODE3Ny1hMmYxN2NmNTU0YjEiLCJhdXRoZW50aWNhdGlvblR5cGUiOiJQQVNTV09SRCIsImVtYWlsIjoibXNyYWdoZWJAdWNpLmVkdSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJyb2xlcyI6WyJTZXJ2YW50Il0sImFwcGxpY2F0aW9uSWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJwZXJzb25faWQiOjF9.aKajyZmIWe0d0ijoV2oTpxVUeQpOieaV5C80SoLqCrA'
puts token
decoded_token = JWT.decode token, hmac_secret, true, { algorithm: 'HS256' }
puts decoded_token
Thanks for the response. Here's one that was just generated and shouldn't be expired:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjllZDRjNjc1NCJ9.eyJhdWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJleHAiOjE1OTQ1MDIwMTQsImlhdCI6MTU5NDQ5ODQxNCwiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIxMzUyOWVkZi05NjFlLTRkM2EtODE3Ny1hMmYxN2NmNTU0YjEiLCJhdXRoZW50aWNhdGlvblR5cGUiOiJQQVNTV09SRCIsImVtYWlsIjoibXNyYWdoZWJAdWNpLmVkdSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJhcHBsaWNhdGlvbklkIjoiOTM4MGQyYzYtYzQzNS00ZWVjLWE4OTctOWVjOWQwODRiY2U4Iiwicm9sZXMiOlsiU2VydmFudCJdLCJwZXJzb25faWQiOjF9.Xf_LYuqhxC1mskoEtKTJogqA_x3PKJlpwkXgRokgI2II tried this following code like yours with the new token and it gives me signature error:
hmac_secret = '1c8e490a-4972-7d73-8935-06621a0a6441' token = 'eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjllZDRjNjc1NCJ9.eyJhdWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJleHAiOjE1OTQ1MDIwMTQsImlhdCI6MTU5NDQ5ODQxNCwiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIxMzUyOWVkZi05NjFlLTRkM2EtODE3Ny1hMmYxN2NmNTU0YjEiLCJhdXRoZW50aWNhdGlvblR5cGUiOiJQQVNTV09SRCIsImVtYWlsIjoibXNyYWdoZWJAdWNpLmVkdSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJhcHBsaWNhdGlvbklkIjoiOTM4MGQyYzYtYzQzNS00ZWVjLWE4OTctOWVjOWQwODRiY2U4Iiwicm9sZXMiOlsiU2VydmFudCJdLCJwZXJzb25faWQiOjF9.Xf_LYuqhxC1mskoEtKTJogqA_x3PKJlpwkXgRokgI2I' puts token decoded_token = JWT.decode token, hmac_secret, true, { algorithm: 'HS256' } puts decoded_token -
Manually verifying a JWTposted in Q&A
I have an access token that is signed by a HS256 signing key. When I go to my rails backend and use the JWT library to decode it and verify it is a valid token signed by FusionAuth it is return Signature Verification Error. Am I doing something wrong?
This is my rails code to decode and verify that the JWT is valid:
JWT.decode(access_token, signing_key, true)This is my default signing key (Yes I know it is insecure to share this, but it's a dev server not production and I will change it after this):
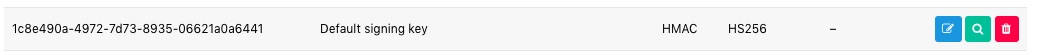
(Signing key in text):
1c8e490a-4972-7d73-8935-06621a0a6441And here is an example JWT that was issued:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCIsImtpZCI6IjllZDRjNjc1NCJ9.eyJhdWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJleHAiOjE1OTQ0ODk5NTMsImlhdCI6MTU5NDQ4NjM1MywiaXNzIjoiYWNtZS5jb20iLCJzdWIiOiIxMzUyOWVkZi05NjFlLTRkM2EtODE3Ny1hMmYxN2NmNTU0YjEiLCJhdXRoZW50aWNhdGlvblR5cGUiOiJQQVNTV09SRCIsImVtYWlsIjoibXNyYWdoZWJAdWNpLmVkdSIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJyb2xlcyI6WyJTZXJ2YW50Il0sImFwcGxpY2F0aW9uSWQiOiI5MzgwZDJjNi1jNDM1LTRlZWMtYTg5Ny05ZWM5ZDA4NGJjZTgiLCJwZXJzb25faWQiOjF9.aKajyZmIWe0d0ijoV2oTpxVUeQpOieaV5C80SoLqCrAI don't know how to further debug this. Any help appreciated, thank you.